Key Takeaways
- SBOMs (Software Bill of Materials) are crucial for ensuring security in embedded systems, providing clear traceability of all software components. This enables organisations to verify integrity and efficiently monitor vulnerabilities.
- High-profile incidents like the Log4J vulnerability highlight the risks of hidden dependencies and demonstrate why maintaining an accurate SBOM is vital for rapid response and mitigation.
- Implementing and maintaining SBOMs aids compliance with industry certifications and regulations, reducing the risk of costly fines for non-compliance.
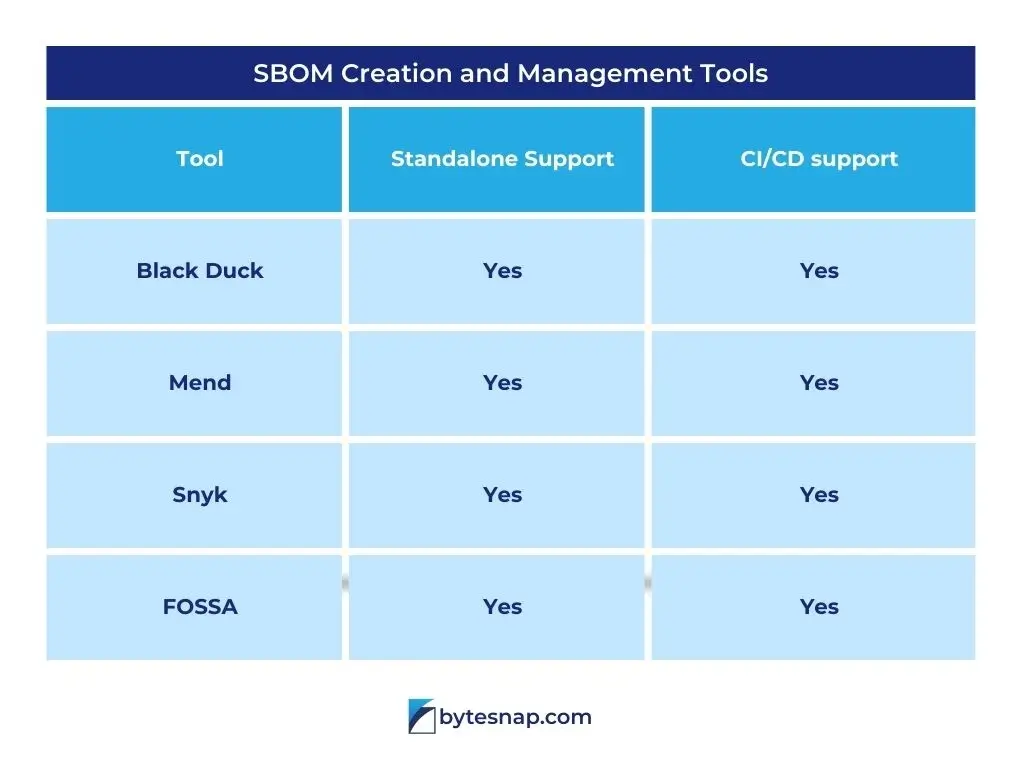
- Tools such as Black Duck, Mend, Snyk, FOSSA and integrated solutions from GitHub/GitLab simplify SBOM creation and management, accommodating both standalone use and CI/CD workflows.
- Regularly updating and validating your SBOM is essential—the effectiveness of SBOMs depends on disciplined, ongoing management rather than occasional, rushed updates.
- Educating and upskilling teams on SBOM practices fosters organisational transparency, smoother certification processes, and strengthens overall cybersecurity posture.
Q: Do I need an SBOM for embedded system security?
Yes, you need an SBOM (Software Bill of Materials) for embedded system security. SBOMs enable you to trace all software components, meaning businesses can verify integrity and keep track of vulnerabilities within their systems. Keeping an up-to-date SBOM allows engineers to quickly identify and mitigate any software issues as soon as a vulnerability arises.
Q: What do SBOMs have to do with compliance with industry regulations and certifications?
A: Keeping a regularly updated SBOM helps organisations to stay compliant with industry regulations and certifications. This means they’ll be less at risk for expensive fines for non-compliance.
Q: Which SBOM tools are best for embedded systems development?
A: Solutions like Black Duck, Mend, Snyk, FOSSA, and integrated offerings from GitHub or GitLab simplify SBOM generation and management for both standalone projects and CI/CD workflows.
Q: Why do I need to update my SBOM?
The more frequently an SBOM is updated, the more useful it is. It’s important to regularly update and validate, because sporadic or rushed changes to an SBOM result in ineffective protection of software assets.
Q: Why should I teach my team SBOM best practices?
By teaching and upskilling your teams on SBOM best practices, this should lead to better transparency, smoother certification processes and an overall boost to your product’s cyber security.
Introduction
An SBOM (Software Bill of Materials) documents all the software components used to create a product, from development tools like IDEs and compilers, through to libraries and their dependencies.
The point of an SBOM is to enable complete traceability of the software stack, which enables verification of tool integrity and vulnerability monitoring.
In November 2021 the logging tool Log4J was discovered to have a serious security issue. Log4j was a dependency for many popular libraries used by professional businesses and even government agencies.
Therefore, this security issue found its way into a large number of software applications. Due to this the vulnerability spread wildly, leaving millions of computers open to attack.
With new security regulations coming in the near future, SBOMs are becoming more and more vital to embedded software development.
EU CRA, US EO14028, EN303-645, and IEC62443 are just some of the regulations that require SBOMs to be implemented in embedded systems.
Contents
What is an SBOM?
Overview
An SBOM can be likened to an ingredient list of an item of food you buy in the supermarket- You can see exactly what’s going into your food, and spot if there’s anything that might cause problems.
In the same way an SBOM allows you to trace back everything that’s gone into making a piece of software. If a vulnerability is discovered in a library that may be relevant to software you’re using, you want to be able to find out immediately whether that library is used in the application.
SBOMs are a vital part of security strategy. Without the traceability enabled by a well maintained SBOM, vulnerability management becomes a challenge, especially if your response team is separate from your development team.
An SBOM should typically contain at least:
- A version number
- Name
- Source location
- Hash for integrity verification
- License details
For every component of the software you’re developing. There are several different formats for SBOMs, including SPDX, CycloneDX and SWID, each of which have different advantages depending on what you need. It’s worth investigating which of these is best for your own requirements.
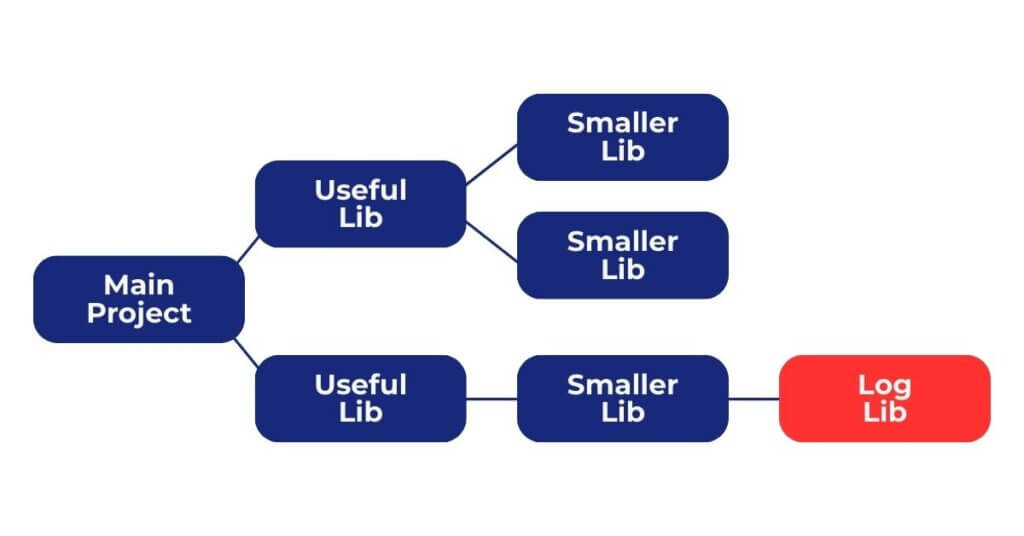
Why SBOMs matter for Embedded Systems
When developing an embedded system, maintaining an SBOM can assist you in several key areas. Security is important in any application, and embedded systems are no exception. When developing an embedded system you will inevitably be using third party software- IDEs, compilers and libraries are all essential in the development of these systems. Using an SBOM ensures that you have a comprehensive list of these items that can help you in several key areas:
Improve Supply Chain Security
If you know exactly what’s gone into your project and can find it out any time you ensure that you can identify any cybersecurity risks that may be introduced in any of these components.
Save Time in Projects
If a vulnerability is discovered in a library online, if you don’t have an SBOM it means your team have to trace back your software manually to find out whether this affects you. With an SBOM it’s a much simpler process: Review the SBOM, and take action if required.
Help with Decision Making
Many of the tools for generating SBOMs also help you make your decisions when choosing software to use. They may perform scans of software or repositories, or provide other information to help you decide what components you can implement into your project, which in turn saves a lot of time and effort from your dev team.
Your Future Team will Thank You
Say ten years down the line a vulnerability is detected in a component of your software, an SBOM will assist your response team in quickly and effectively taking action to resolve it. This is crucial as we look forwards, as cybersecurity becomes ever more important day by day.
Regulatory Landscape and Compliance
SBOMs don’t just help with efficiency and security. In some cases, they may already be required legally. US Executive Order 14028 was issued by Joe Biden back in 2021 and is focused on strengthening cybersecurity across the US. Similarly, the EU Cyber Resilience Act was introduced in 2022 by the European Commission. These acts contain rulings for new cybersecurity regulations on software in the US and EU respectively.
Both of these regulations make explicit mention of SBOMs and their usage in software products. This means that if you want to develop an embedded system in the US or EU, it may soon be a requirement for you to use an SBOM within your development to ensure you meet compliance with regulation.
An SBOM can also help to maintain approved vendor lists by aiding with verification that your vendors are complying with industry certifications and regulations. They also aid transparency for your own certification, meaning that it saves you time and money to meet certification requirements yourself.
Failing to meet these requirements could result in your company being fined up to 4% of your turnover for non-compliance!
SBOM Creation and Management Tools
There are several different tools to aid you in creating and managing your own SBOMs which are good for slightly different purposes, including Black Duck, Mend, Snyk and FOSSA.
GitHub and GitLab also have built in tools to generate SBOMs directly from your repository.
Tools like this can be built into your workflow or run standalone, though to maintain good standards throughout development it’s a good idea to use these in a structured manner throughout the project as opposed to running it retrospectively at the end.
These tools are of course useful for generating and maintaining SBOMs, but also tend to contain utilities to assist you with other development tasks such as checking compliance for open source components, plugins for IDEs, continuous monitoring of dependencies and report generation for audits.
Implementing SBOM in Your Organisation
Generally, SBOM implemention needs to be integrated into your development workflow as opposed to being addressed retrospectively. Simple tracking can be managed by using a spreadsheet or similar software during development. At ByteSnap we require customer authorisation and a license agreement to use any outside source code. However, the more dependencies you rely on the more complicated this process gets.
Tools such as those we highlighted above can help you and your organisation straighten out and simplify this process. You can automate the process by making these tools auto generate an SBOM after every build. It’s good practice to regularly cross reference these auto generated SBOMs with a manually generated one to ensure they are accurate.
At the development level you should be mindful of the dependencies you use, and should keep track of the ones you choose using an SBOM. As the project develops, this SBOM should be tracked and updated frequently.
At a management level you should try to ensure that all members of the project not only understand how to maintain and use an SBOM, but also to understand why they should be keeping one.
Training and upskilling your team on this is vital to keeping a clean record of the resources your staff are using. You should also incorporate SBOM creation and maintenance into your workflows and processes as a guide for your team to follow.
Overcoming SBOM Implementation Challenges
SBOMs can be a frustrating process to maintain, especially if done manually. Continuously updating and cross referencing the dependencies is an understandably tedious task. Some may see it as a waste of time and therefore money to maintain an SBOM. However when you add tools into the calculations, the difficulties become much more manageable.
Obviously tools have their own subscription or use costs, so for your projects you’d need to do a cost to benefit analysis. Generally manual SBOMs will work out alright for lower complexity projects, as there’s less components to manage. But as the complexity increases tools become more valuable as they reduce the time spent to maintain the SBOM.
Generally, whatever method you decide to implement, it will get easier if you integrate it into your workflow and processes. It’s a bit like housework: A little bit of work every week means things don’t pile up and you don’t end up doing it all at once when you expect a house visit!
Ensuring you generate an SBOM after every build means that when you’re due an audit or a customer asks to review it, you aren’t rushing around to put it together all at once.
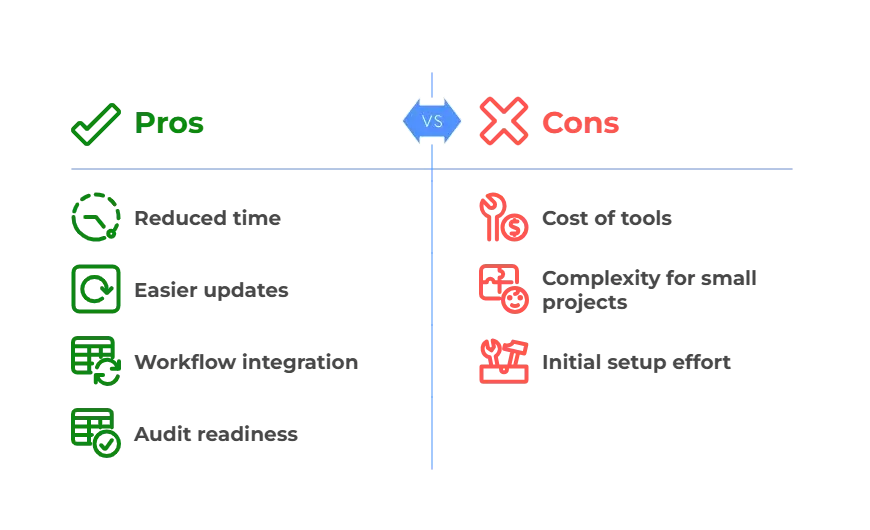
Best Practices for SBOM Implementation
An SBOM’s effectiveness will vary depending on how you work with it. If you update it irregularly and poorly you can’t expect it to be of any use when you finally need to make use of it.
Instead, you should follow good practices to ensure that you make the most out of them:
- Integrate SBOM creation into your Secure Software Development Life Cycle (S-SDLC). By ensuring it’s integrated into your processes you should ensure that everyone is familiar with SBOM implementation and usage.
- Keep it regularly updated and validated. By keeping it up to date at all times you ensure you don’t have to do it all at once and risk making a mistake or generally just wasting time.
- Use automated tools to increase efficiency. These will help reduce human error and save time during development.
- Establish a process for dealing with vulnerabilities identified via your SBOM. When a vulnerability is identified any time wasted is a threat to anyone using your software. You must ensure that you have a procedure in place in the event of a vulnerability.
- Generally the most efficient way to maintain an SBOM is to integrate it with CI/CD processes, and have a manual review step to ensure it’s correct.
Following these rules should ensure that implementing and using an SBOM is as painless and useful as possible.
Conclusion
SBOMs are becoming an increasingly important component of embedded software design. Not only do they increase your efficiency, they also ensure you can respond quickly to security vulnerabilities which is crucial given the nature of our digital landscape. Furthermore, due to new legislation coming in around the world, an SBOM is no longer a nice-to-have component. It’s vital that you take action now to prevent cybersecurity vulnerabilities from causing problems in the future, and avoid fines and penalties.
Next Steps for Your Embedded Systems Security
FAQs
1. How can SBOMs help me meet project deadlines?
SBOMs can help your team to keep a clear inventory of all the components in your project. This will help manage your dependencies and help to identify conflicts and security vulnerabilities to deal with them early before they become a problem. This will save time and help you complete projects without unnecessary time wasting.
2. How do SBOMs integrate with our existing supplier management processes?
SBOMs can be used within your supplier management processes to automate validation of components, to ensure everything you’re putting into your project is secure, safe, and won’t cause any conflicts.
3. What skills does my team need to effectively implement and manage SBOMs?
There are no specialised skills required to implement SBOMs into your processes at the base level, but it’s worth ensuring your project teams are aware of the processes. If you’re doing it manually, this is the case. Using automated tools may require some training on how to set them up, but it varies depending on the tool you use.
4. How can SBOMs help me stay up-to-date with industry trends in software security?
SBOM tools allow you greater transparency regarding the components you use. They allow you to see any known vulnerabilities in components you may wish to implement in your project, as well as other vital information.
5. How can SBOMs contribute to overall project efficiency and productivity?
SBOMs allow you to check out the components you’re going to be introducing into your project quickly and without the hassle of manually cross checking for known vulnerabilities. They also allow you to respond much quicker in the case that a security problem presents itself in the future.

Founded in 2008, ByteSnap Design is an award-winning embedded systems design consultancy, offering a comprehensive range of services across the electronic product development lifecycle.
A highly skilled team of over 40 hardware and software engineers, our expertise spans several sectors, including IoT, automotive, industrial, medical, and consumer electronics.
The engineering consultants on the ByteSnap Editorial Team share their knowledge and practical tips to help you streamline your product development and accelerate designs to market successfully.
With their deep technical expertise and practical experience, they aim to provide valuable insights and actionable tips to guide you through the complex world of electronic product design and development, to help you bring innovative, reliable, and secure electronic products to market quickly and cost-effectively.





